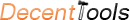
| Queries | Unique users |
Referrers |
Average Click Position |
|
|---|---|---|---|---|
| sans | 2 | 2 | 1 | |
| emails confirmed theft of trade secrets | 1 | 1 | 9 | |
| how to get back on internet after an intrusion attempt | 1 | 1 | 1 | |
| ben malisow | 1 | 1 | 13 | |
| steam bath new york | 1 | 1 | 9 | |
| how to create a virus | 1 | 1 | 1 | |
| mentor programs in nashville | 1 | 1 | 3 | |
| macro virus | 1 | 1 | 10 | |
| network intrusion detection system | 1 | 1 | 2 | |
| encase certified | 1 | 1 | 55 | |
| microsoftsecurity | 1 | 1 | 25 | |
| what is the policy process in developing educational policies | 1 | 3 | 5 | |
| becoming a forensic | 1 | 1 | 4 | |
| sans top 20 | 1 | 2 | 1 | |
| best price and symantec guide to home internet security | 1 | 1 | 29 | |
| best all in one effective computer security program that uses low system and memory resources | 1 | 1 | 1 | |
| anthony kolstee | 1 | 1 | 9 | |
| corporate espionage | 1 | 1 | 1 | |
| - | 1 | 1 | 1 | |
| internet security settings | 1 | 1 | 9 | |
| top 20 | 1 | 1 | 1 | |
| certification for bank security officer | 1 | 1 | 16 | |
| surveys | 1 | 2 | 112 | |
 |
||||